统一身份认证授权登录
从3.1.0版本开始,集成统一身份认证登录功能,用户可以通过统一身份认证账号登录本系统(pc端管理平台和移动端)。
1 应用配置
- 登录统一身份认证系统管理端,新增相关应用,配置参考下图:
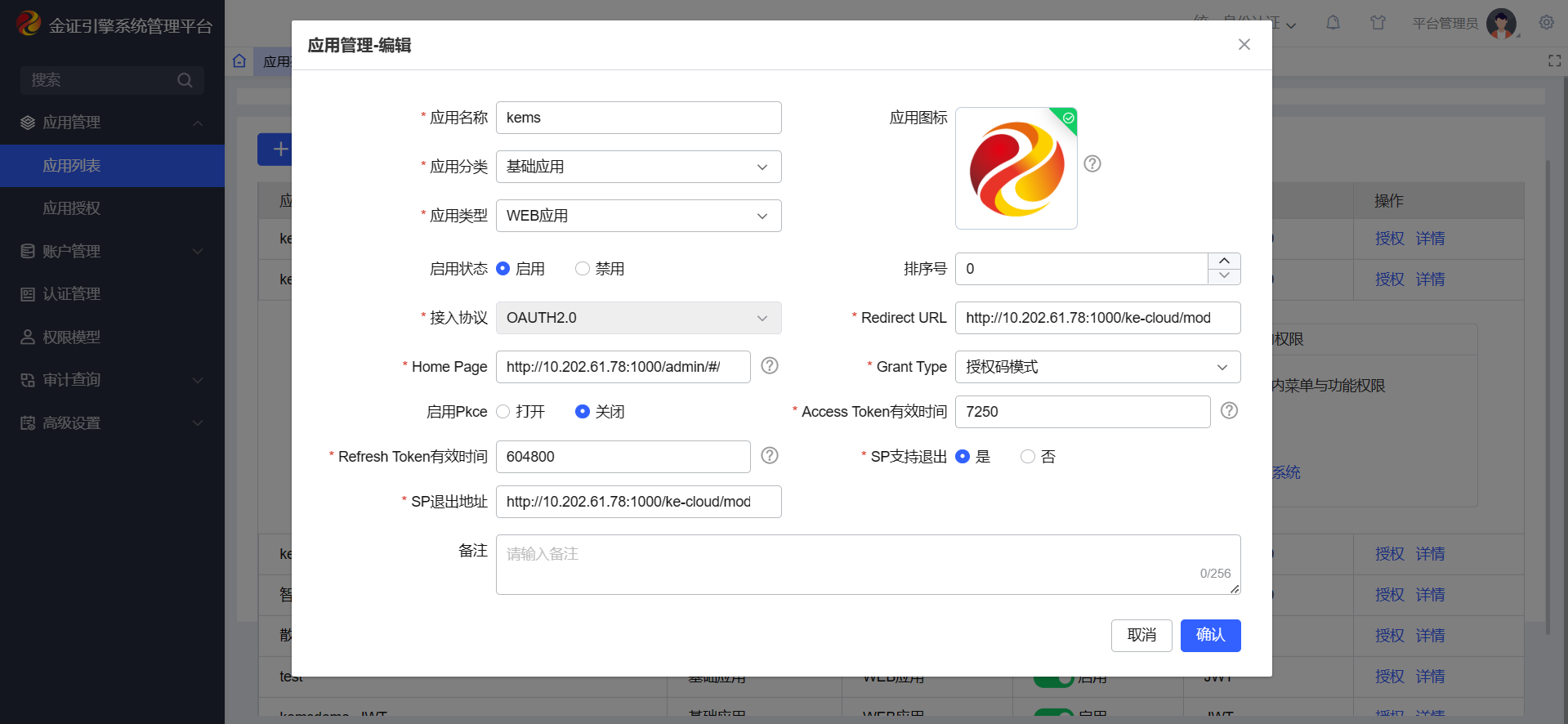
- 点击应用授权,将该应用授权给相关用户,然后点击保存。
2 gateway配置
- auth.yml
koca:
security:
auth:
randomCodeSwitch: true
ignoredUrl:
- /module-system/oauthAdmin/**
- /module-system/idaas/api/getSign
multi-login:
- type: loginForIdaas
login-url: /auth/loginForIdaas
strategy-name: idaas-tgc #idaas tgc登录策略
auth-url: http://module-system/idaas/api/login #idaas tgc登录校验URL,服务调用
#auth-url: url:http://localhost:8003/idaas/api/login #添加前缀url:,则直接调用该地址
token-enabled: true
- type: loginForIdaasH5
login-url: /auth/loginForIdaasH5
strategy-name: idaas-tgc-h5 #idaas tgc h5 登录策略
auth-url: http://module-system/idaas/oauth2/login #idaas tgc登录校验URL,服务调用
#auth-url: url:http://localhost:8003/idaas/oauth2/login #添加前缀url:,则直接调用该地址
token-enabled: true
3 module-system配置
- application.yml
# 服务间鉴权
request:
credential:
exclude-path-patterns:
- /idaas/oauth2/login
enabled: true
新增idaas.yml文件
部分地址url同步骤1所配置,client-key和client-secret请在步骤1中复制
idaas:
#oauth2协议配置
oauth2:
client: #业务系统接入接口配置
client-id: d749ac2cc53a4a4b905cc9a1cc9d4637
client-secret: e98a4d4d92804c4f83073dc85d78ec52
redirect-url: http://10.202.61.78:1000/ke-cloud/module-system/oauthAdmin/redirect
grant-type: authorization_code #implicit authorization_code
login-page-url: http://10.202.61.78:1000/admin/#/ssologin #登录页
home-page-url: http://10.202.61.78:1000/admin/#/ #主页
enable-pkce: false
server: #统一认证平台配置
authorization-url: http://10.202.61.78:8080/module-mgr/oauth/authorize
token-url: http://10.202.61.78:8080/module-mgr/oauth/token
refresh-token-url: http://10.202.61.78:8080/module-mgr/oauth/token
user-info-url: http://10.202.61.78:8080/module-mgr/oauth/userinfo
logout-url: http://10.202.61.78:8080/module-mgr/oauth/logout
user-list-url: http://10.202.61.78:8080/module-mgr/oauth/getUserList
#jwt协议配置
jwt:
client: #业务系统接入接口配置
client-id: 14b115b0c1a64aac8f6ec972cce680f5
redirect-url: http://10.60.1.13:10083/ke-idaas-auth-demo/jwtOauth/redirect
target-page-url: http://10.60.1.13:10083/ke-idaas-auth-demo/jwtOauth/home
public-key: '{"kty":"RSA","kid":"14b115b0c1a64aac8f6ec972cce680f5","use":"sig","alg":"RS256","n":"zpP85O_wa2LNfQtVzxkPs8s84jvUW9WBpm5s_HqwPo9oGAcnmBnbZXmrvlG8RvSmZvQzWE_yk-1hR8SLtJHtpBlvQdVywbvCOMWiSwnRfnYX2j2eKdPGOY2fRlq-WqtqY41Un_zdZpPYa4NURkRJXxFfZW7HQcr8dm-ERG-1TDzXpvRMJaWgal2RiofKriKXwVtRz7KVop3pZyWovR_oX2IGfYTLMkkzZ3B-awbnBEOjDJAW7NYzqGx-GH0EqqyUrSOl390L0Eehtva3xbry4m3LwncVBSvxKXZswaSopZBkZZMtTehhd7C9qwunkrdcvDey8nGT-zyTfZZB3wINew","e":"AQAB","d":"UKidxPIeqH9ShrGHVq6NYAFKC3ea6iSKU-an7UkmSbcKyN76SbxG2u9P7KbTYc0ir-5HogLNT48PPctzVRTpefpoY4cpIJXkNvCL9sqlnsATfiYy_Ffw_QXcG8dQrexiRO6pDTLZa7TsesYzgKAnGdSZr-w6JulP_Bp8xY_sdRBU-MGMOuuLNxyRMHMkfrUZ-t7Cz_ckJdb4kQmIuTInO56vMU2orPcPtgihem7Oby350uuih1R_SFA9Sy31u17mxppqCrHJCIc9ezGFmzBV2NCh1i_gd1ZXSstjdRYsBK7VNhpbN6Lq98VL0A6P59aahn85ROttF8me93hpGlfXAQ","p":"5-JRi0DTQ9eGuMIiz1PdPJMyl6Xd0jvFR7pfh09aWT64y35nZ_fQu5C0fmqi0peYD-B7qYugO4kEXSaAixP0ivAnPO4hHoIrOB5rA55m5iWC5cn-S693EN6aEJAVEFX6vXZ-qOPwxpo2roqI4XtXXKkhXmIzP2XruSYpnnbuNvs","q":"5A_sQ-U78hTOqQg38_sfw12IM47szW-tx3DoP2T1i6DbYkYG2R9xDFTnuUKvw31nPtjUVdHosyzJi2MFsyZxvxIzYIohnQcJp4IWBnEe4GW8PePixoV9L5hbdlR_6DyWgOXwx1e_fqqIQmU_IpZI0RLHlC3qDdc6HZboam89u4E","dp":"BUS2F5Tcd_EgpXf7tHwyTZsGjj19gbZL8CpC218pLVfoeO8hSFJwEqLiBvFDS8eX89xk0uBSPqgJSliCmSZV6wYzzgWXCQtqEfdW9RkXO2lkxPXG6k9NRDvagj_TyrA5Zy6XCB1NriV40pRhMcZMoNVS5cMTaQBWz7kXPvtyxBs","dq":"hEZD94EuSpMM5fcRVN4TJyHJjHXaHLEobqOq4JHy5MAwXghVknrs-4UHPWlTPiQuzMHALeJof_t7DfAp7yVeFb89s0GKi2P4koIdujDEAsye6JqS_ieQWxmX-sK5yP3TIQG8rDHVrGbGTxQgETRvGWw1-1jCBrMNTvom5QyOFoE","qi":"Um45lyjTyis7PcWq9SU4DNRdzA4kNyqcBfspGgv0PHKUP_a_QUMYf4gqfrd6Mc_D1grw0RXKk5eK5HP7b0oPwJcBpuzSfufBJ0i3-P8pQjKdIRNItZBfVfChO5JNlT4mnh8mzGDg7oPUdjbyR9zdhEI0OahSo1p0evPp5z3P9sw"}'
get-token-url: http://10.60.1.13:10083/idaas-auth-demo/#/uvCenter
server: #统一认证平台配置
authorization-url: http://10.60.1.13:10081/ke-idaas-auth/module-mgr/oauth/authorize
logout-url: http://10.60.1.13:10081/ke-idaas-auth/module-mgr/oauth/logout
#数据同步配置
dis:
is-sync: true #数据同步开关,true同步,false不同步
server-url: http://10.202.61.78:8000/ke-idaas/module-di/dis #统一认证服务端数据同步地址
app: #应用配置
client-key: 946c3dadb10c484b8b5b222dfa2077e1
client-secret: 8ee51ffcf9dc478fabad0b9e0c7450c9
pm: #权限模型配置
app-key: 38da313ea9584d0a9fb9575eddffb640
app-secret: 5cf2e0a356ba43b485dd525915dedcf0
jwt:
#长度要>=64,否则createJwt()的HS256会失败
secret: e5278e6fc525be88c1bf39f0f283a9896a712719f8d2d8d3676fa41552fgsw5d
ttl: 360000000
header: x-access-token
- 新增idassapi.yml文件
idaas-api:
get-sign-url: http://10.202.61.78:8000/ke-idaas-auth/module-mgr/oauth/third/getOauthSign
login-by-phone-code-url: http://10.202.61.78:8000/ke-idaas-auth/module-mgr/oauth/third/login/phone/code
login-by-password: http://10.202.61.78:8000/ke-idaas-auth/module-mgr/oauth/third/login/password
get-user-info-url: http://10.202.61.78:8000/ke-idaas-auth/module-mgr/oauth/third/getUserInfoByAccessToekn
mutil-client:
- client-id: d749ac2cc53a4a4b905cc9a1cc9d4637
client-secret: e98a4d4d92804c4f83073dc85d78ec52
enabled: true
- client-id: b4d3102dbc1740229b5bce019145c91f
client-secret: b4d3102dbc1740229b5bce019145c91f
enabled: true
4 前端配置
修改前端工程中配置文件public/config.json,IDAAS_LOGIN为true时开启统一身份认证。
"APP_SETTINGS": {
"IDAAS_LOGIN": true
}
5 登录方式
- 1、通过原系统登录网址登录:金证引擎系统管理平台
- 2、通过统一身份认证系统认证端登录后点击应用(步骤1里新增的)登录:金证引擎统一认证平台
- 3、系统原账户只能通过方式1登录,统一身份认证用户初次只能通过方式2登录,登录后会注册一个新的默认用户(已存在则不注册直接登录,默认用户包含默认角色和默认机构以及相应菜单),然后后续通过方式1和2都可登录。
注意:由于网关和系统管理这部分新增代码相对较多,此处暂不提供,如有需要请联系开发人员。